Last Updated on April 3, 2021 by Larious
Hacking is of two types – Ethical and Unethical. Ethical hacking involves founding security flaws in software, servers, etc., whereas unethical hacking is done for illegal purposes. On unethical hacking, the victim remains unaware until they have been hacked. It’s often done to break into an account, network, system to steal sensitive information or money.
Phishing is one of the popular unethical hacking techniques used by hackers. Phishing is a type of hacking in which an attacker sends a link/email to the victim. The link/email looks legitimate to the recipient, making them believe that the link or email is something they want or need. Phishing email often resembles itself as a bank request, a note from someone in their company asking for monetary help, etc.
Table of Contents
Protect Yourself From Phishing Hacking Attacks
In this article, we have decided to share some of the best methods to protect yourself from Phishing hacking attempts. The ultimate goal is to make our readers aware of various hacking attempts, and this time it’s – Phishing Attack.
Always Browse Securely With HTTPS
If you want to remain on the safe side, you should always use a secure website to browser. Now the main question is how to figure out whether a website is secure or not? You need to look at the URL bar and an ‘HTTPS’ indication. If the website has a security ‘lock’ icon in the browser’s address bar, and the website starts with HTTPS, it’s probably secure.
The modern web browser now blocks website that is not HTTPS secured. Even if you visit a site without HTTPS, never enter personal details like phone number, bank credential, credit card numbers, and all.
Identify Phishing Emails
Hackers often use emails to trap innocents. So, before opening or responding to a particular email, look closely. Does that email look suspicious? Cybercriminals often make silly mistakes in composing phishing emails. Below, we have shared few points that would help you identify a phishing email.
- Copy the name of a company or an actual employee of the company.
- Include sites that are visually similar to a real business.
- Promote gifts or the loss of an existing account.
Check for Type Errors
Well, if it looks wrong, then it’s probably fake. Typos can be a sign that an email is dodgy. Therefore, before making any final decision, make sure to notice the typos. Generally, Phishing campaigns leave traces behind type errors. Check the all-capitals in the email’s subject and a few too many exclamation marks.
Beware of threats and urgency.
Sometimes cyber criminals might also ask you to change your passwords quickly. However, you should be aware of such actions. They would provide you a webpage that requires you to enter the old password to create a new one. As soon as you enter the old password, you will be hacked. So, beware of threats and urgency. To be on the safe side, you should always double-check whether the event triggering the sense of urgency is real or not. You can check the tech news website to confirm such events.
Share your Details Only Via Phone Or Trusted Websites
If you have to share your data with anyone urgently and don’t have any reliable means of communication, you can rely on phone calls. Phone calls were more secure than social networking sites that you use today. Even social networking sites log your activity to enhance their experience. In the past, we have seen lots of popular social networking sites, and instant messaging app getting hacked like Twitter, Linkedin, and even Telegram in 2016.
Use Antiviruses With Internet Security
Many antiviruses scan your computer but don’t protect you against network threats. So, while purchasing a security suite, make sure to buy the one that provides real-time protection, internet protection, and network protection. You can either use Avast Free Antivirus or Kaspersky Security cloud to protect your computer. Both of them were free to download, and they offer real-time protection against all sorts of security threats.
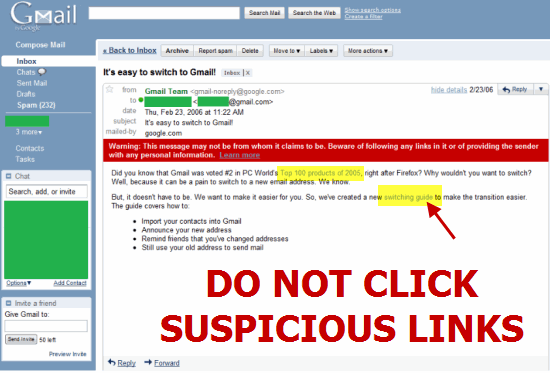
Avoid The Unknown Links
Today many attackers will send you a phishing link that will be just for the phishing attack, and you get hacked via an opening that links on your device. So, before clicking on any link, double-check the link structure. Look for suspicious things like a spelling mistake, wrong sentence, and more.
Look for Clones
Creating clones for each website is very easy. So, sometimes the link you’ve clicked might be a trick from fraudsters to hack your account. Before entering your account credential, double-check the URL you have been redirected to. If it has any mistakes or looks dodgy, it’s best to avoid it.
Check Your Spam Settings
Some of the email providers allow users to update the Spam Settings. Usually, popular email services like Gmail automatically recognize Spam emails and sends them to the Spam folder. However, not every email service provider is as smart as Gmail, and you need to check the spam settings. Some of the popular email service providers allow users to select the level of spam detection.
Check the App Permissions
Now that we all are connected to social networking sites like Facebook, Twitter, Instagram, etc. It becomes essential to check the app permissions regularly. Facebook apps can be useful and fun, but they also have permission to manage your data. Therefore, make sure to revoke Facebook app permissions if you have stopped using it.
Don’t log in with Services while using Public Wi-Fi
When you connect to a WiFi network that’s open to the public, your connected device, whether your smartphone or laptop, becomes an easy target of cybercriminals. If not phishing, Public WiFi connections can land you on other troubles like data hogging. Hackers can see which websites you are visiting, what you are typing, and more. Cybercriminals might redirect you to a webpage that looks legitimate, but it’s a trap. You might end up entering your details and becoming an easy target for hackers. It’s best to use a mobile connection, even if Public WiFi is available.
Download Software from Trusted Sources
Well, Phishing attacks are mostly seen on computers, but that doesn’t make smartphone users safe. Hackers will try their level best to get your sensitive details. A few sites ask users to sign up and enter the credit/debit card details before downloading software; it’s best to avoid such sites.
As long as you download apps from trusted sources, you are on the safe side, but entering sensitive information on non-trusted sources is merely an open invitation to the hackers to get a hold of your data. So, make sure to download software and Android apps from trusted sources to reduce the risk of phishing attacks.
Check The Reviews
Checking the user reviews before entering sensitive details like banking details, etc., is another best thing that you can do to avoid a phishing attack. User reviews are always the best option to know about any particular website or software. So, read out the reviews or comments, and we are sure that you will get some definitive clues. If you find that many users are complaining about hacking attempts or phishing attacks, it’s better to leave that service or app.
Familiarize yourself with the Website’s Privacy Policy
The majority of commercial websites have a privacy policy that is usually accessible in the web page’s footer or header. Do you need to look for whether the website sells the mailing list? Most users receive spam in their inboxes because they sell email lists with other companies. Some companies can misuse the mail list to send potentially dangerous phishing emails.
Change Your Accounts Passwords Periodically
Changing the passwords of your most used social networking, instant messaging, and banking account is a good security practice. Everyone should make it a habit to change the passwords at regular intervals. However, make sure that you don’t use the same passwords everywhere. To set up a super-strong password, check out the article – How To Create A Super Secure Password To Defeat Hackers
This article is all about How To Protect Yourself From Phishing Attacks. I hope this article helped you! Please share it with your friends also.